Vulnerability Scanning in your CI/CD Pipeline - Part Two
Por um escritor misterioso
Last updated 17 junho 2024

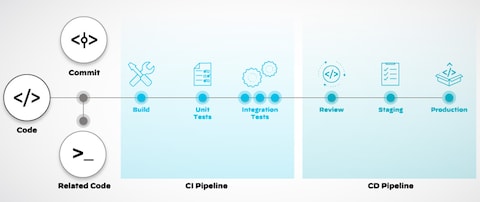
What Is the CI/CD Pipeline? - Palo Alto Networks

Scan for vulnerabilities early to shift security left in CI/CD

How to Add Application Security Tests to Your CI/CD Pipeline

Vulnerability Scanning in your CI/CD Pipeline - Part Two
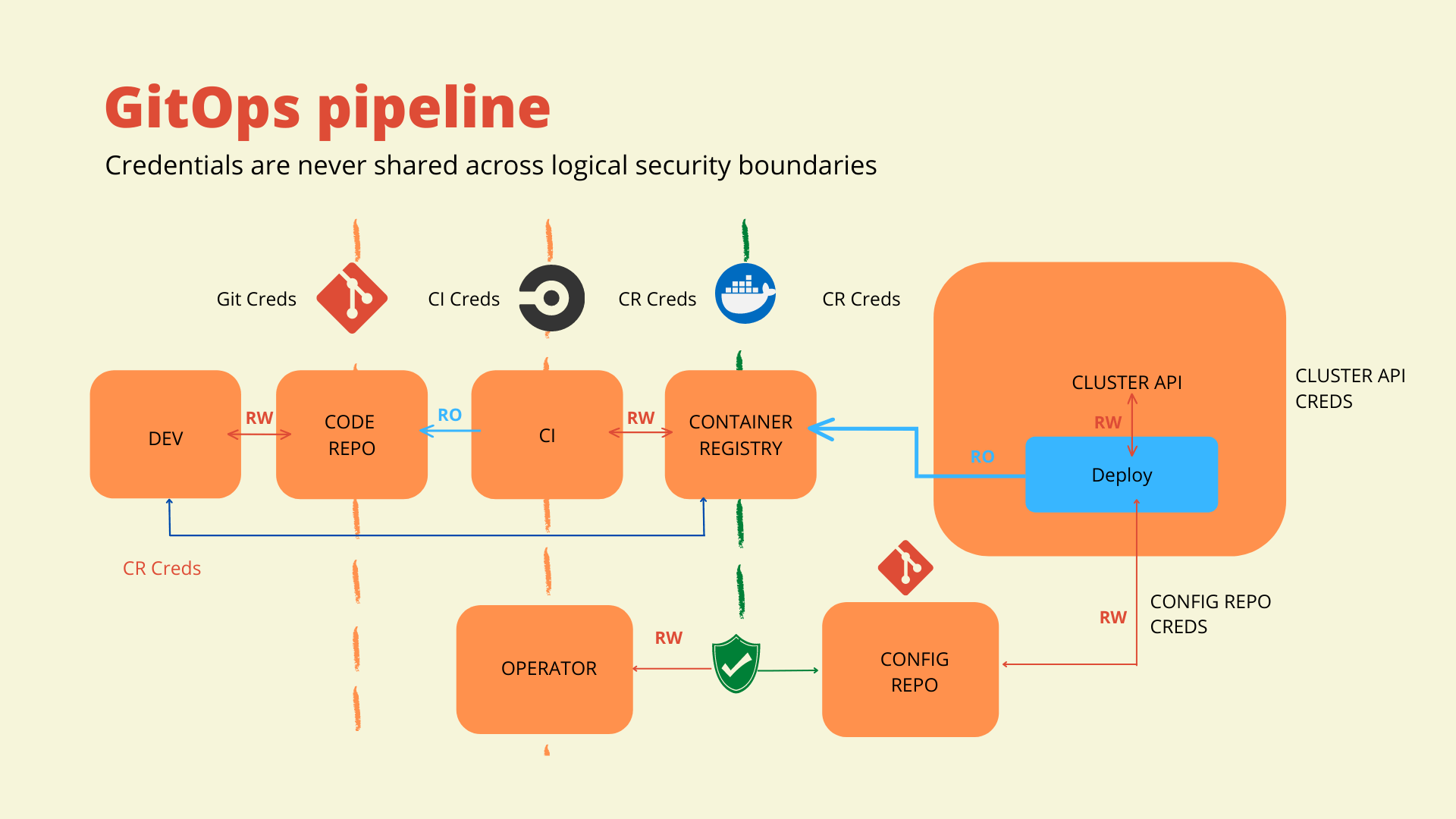
GitOps Approach to Continuous Security to Harden your CI/CD Pipeline
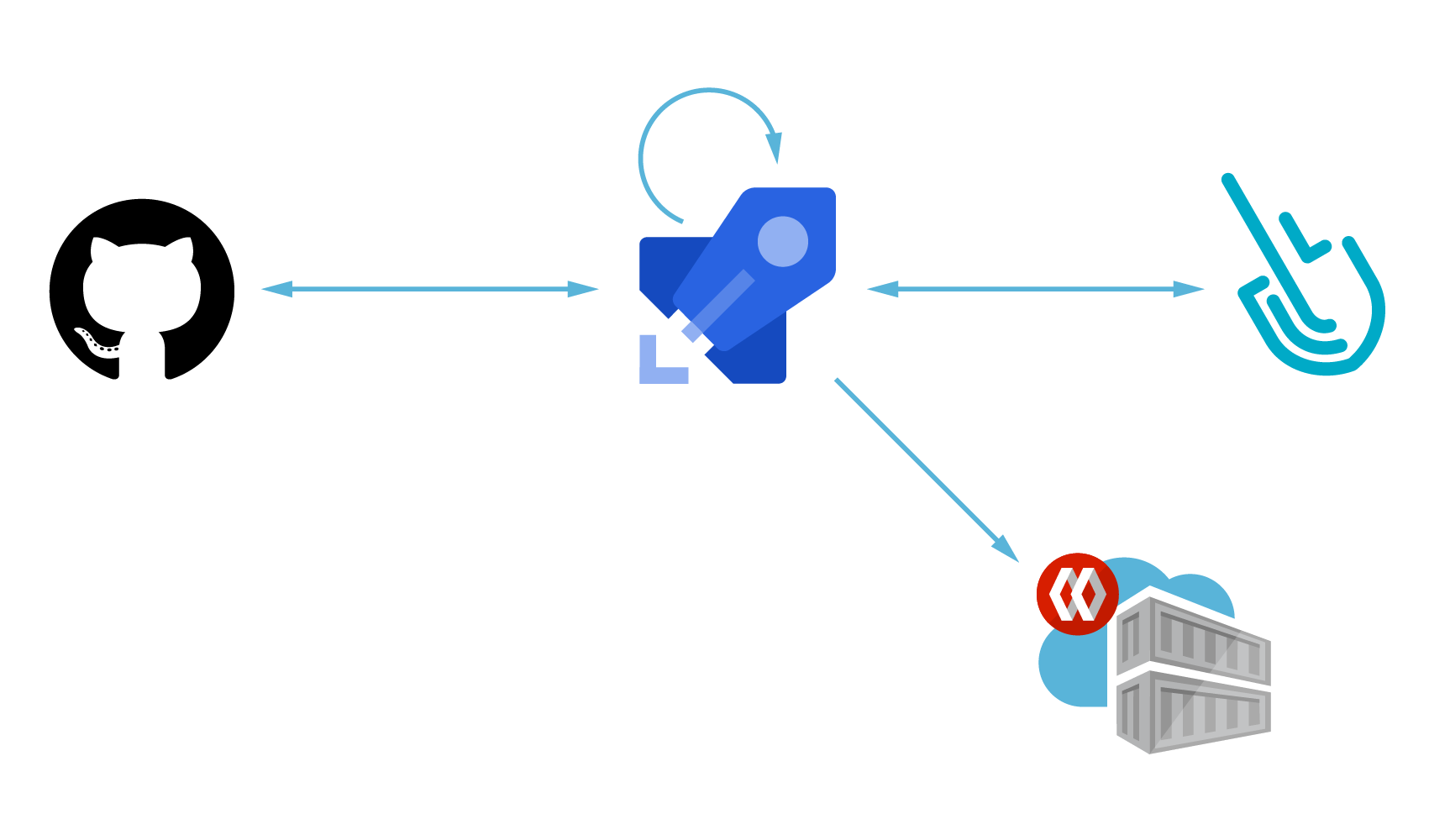
Container Image Scanning for Azure Pipelines with Sysdig – Sysdig

Adding Image Security Scanning to a CI/CD pipeline, by Larbi Youcef Mohamed Reda, alter way

OWASP Top 10 CI/CD Security Risks

What DevSecOps Means for Your CI/CD Pipeline
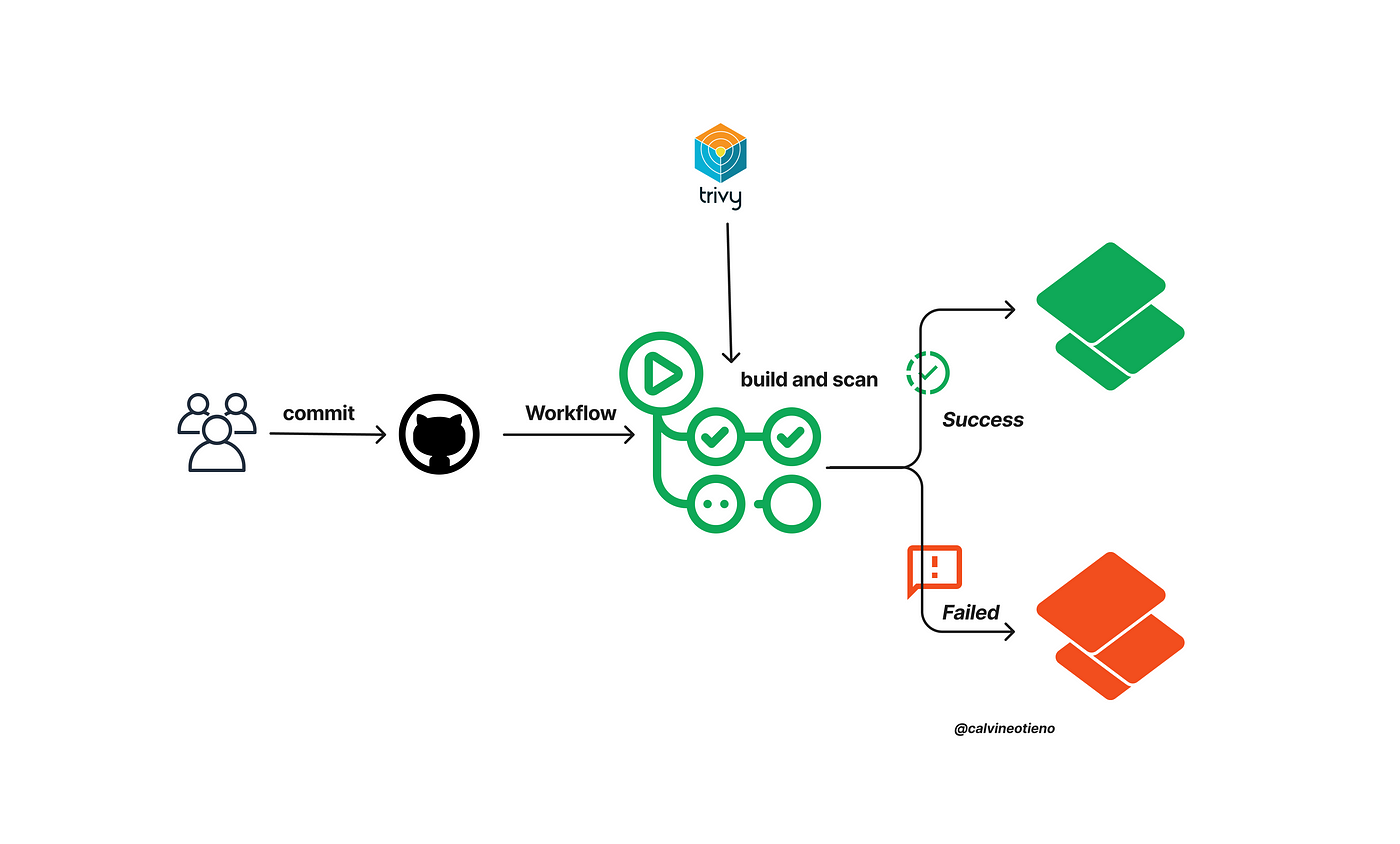
Improving your CI/CD Pipeline: Helm Charts Security Scanning with Trivy and GitHub Actions, by Calvine Otieno
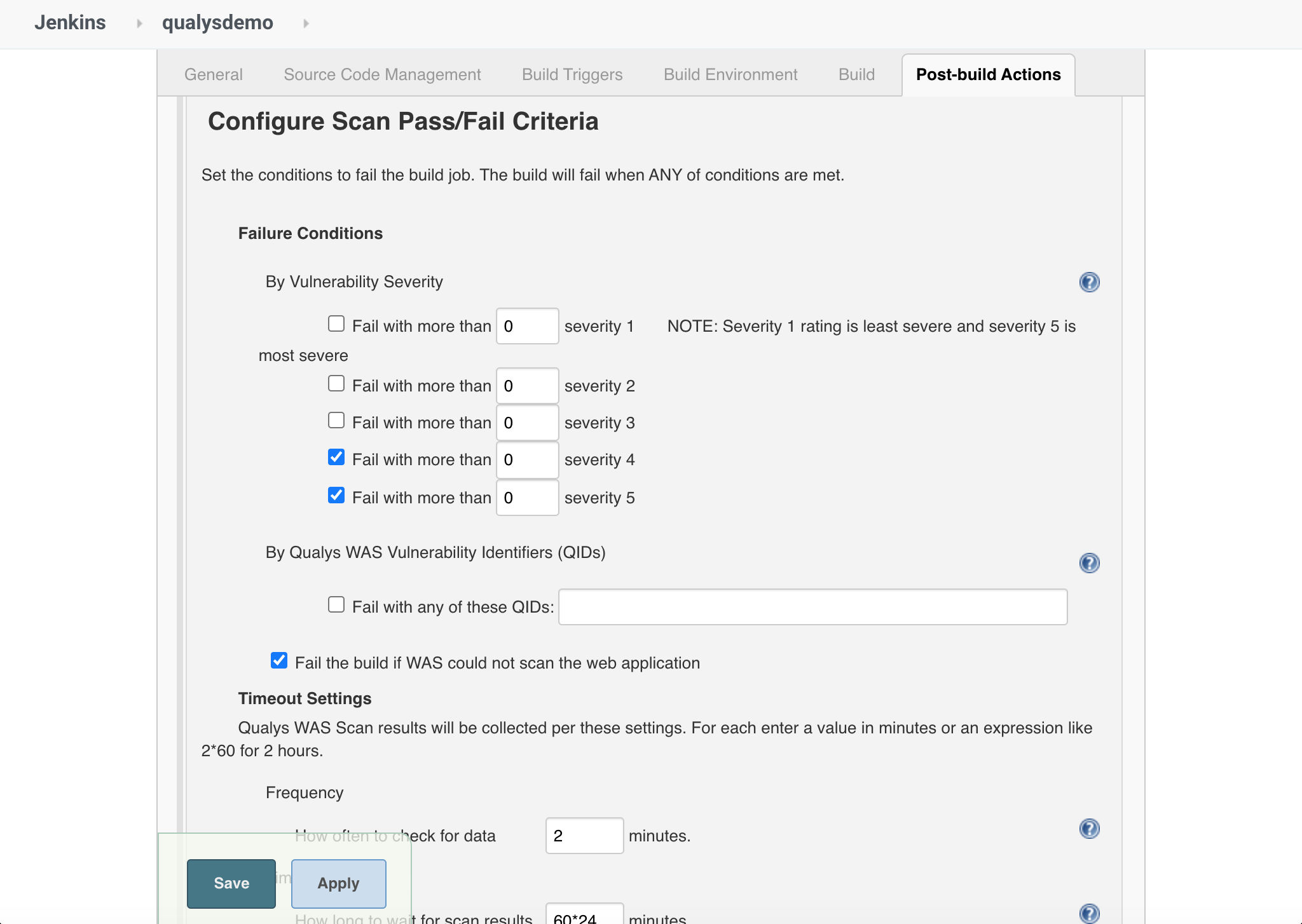
Add Ergonomic Security to Your CI/CD Pipeline
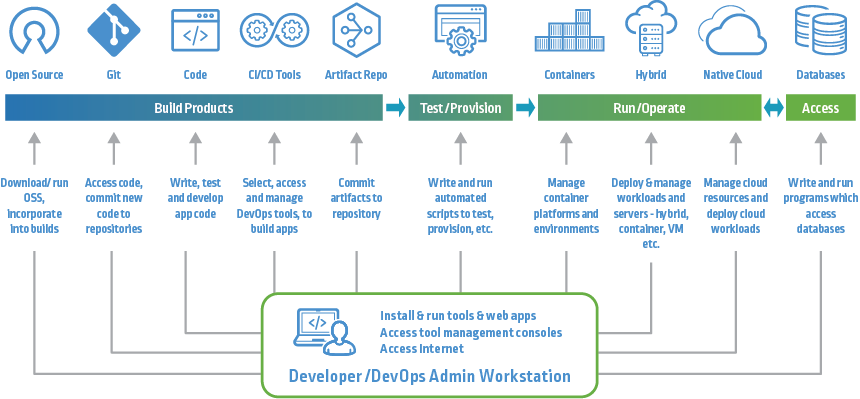
What is CI CD Pipeline? - CI/CD Pipeline Definition
Recomendado para você
-
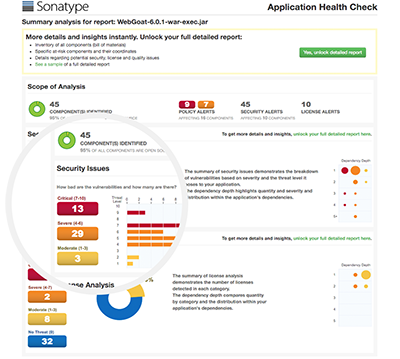 Nexus Vulnerability Scanner17 junho 2024
Nexus Vulnerability Scanner17 junho 2024 -
 NEXUS score vs CT scan findings.17 junho 2024
NEXUS score vs CT scan findings.17 junho 2024 -
 Nexus users face new biometric scanning kiosks at Vancouver International Airport17 junho 2024
Nexus users face new biometric scanning kiosks at Vancouver International Airport17 junho 2024 -
 Leveraging Datature Nexus for Tumor and Anomaly Detection in Medical Scans : Part I17 junho 2024
Leveraging Datature Nexus for Tumor and Anomaly Detection in Medical Scans : Part I17 junho 2024 -
Nexus iOS - Nexus iOS Scan Gauges provide the most17 junho 2024
-
 maven - Why would Sonatype IQ scan report Guava vulnerability when 'mvn dependency:tree' does not show Guava at all? - Stack Overflow17 junho 2024
maven - Why would Sonatype IQ scan report Guava vulnerability when 'mvn dependency:tree' does not show Guava at all? - Stack Overflow17 junho 2024 -
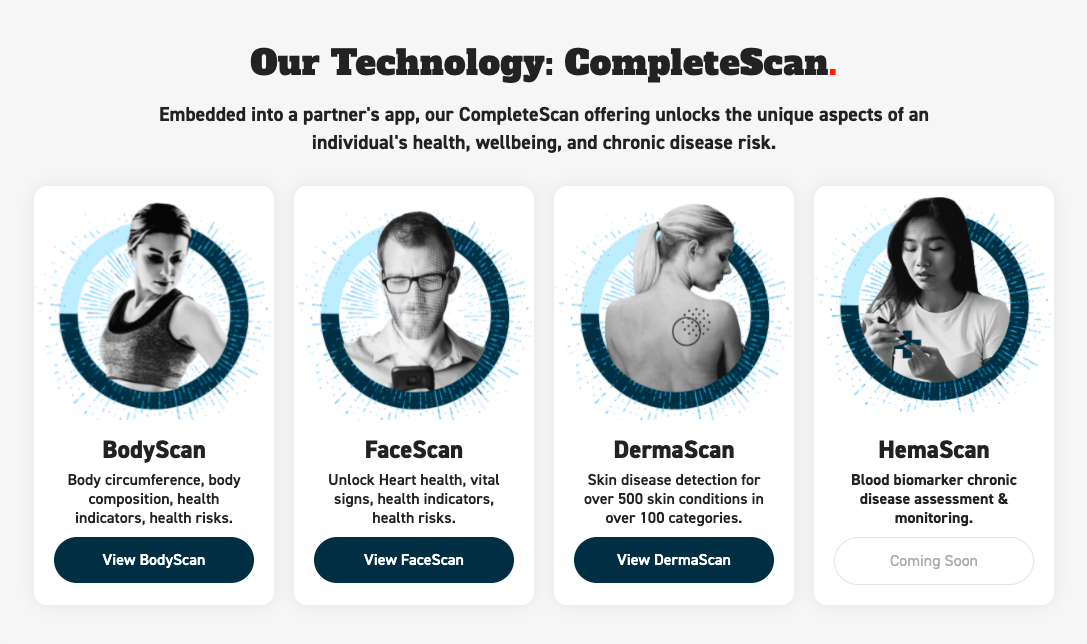 Advanced Human Imaging to finish integration of health screening tech with Nexus-Vita app17 junho 2024
Advanced Human Imaging to finish integration of health screening tech with Nexus-Vita app17 junho 2024 -
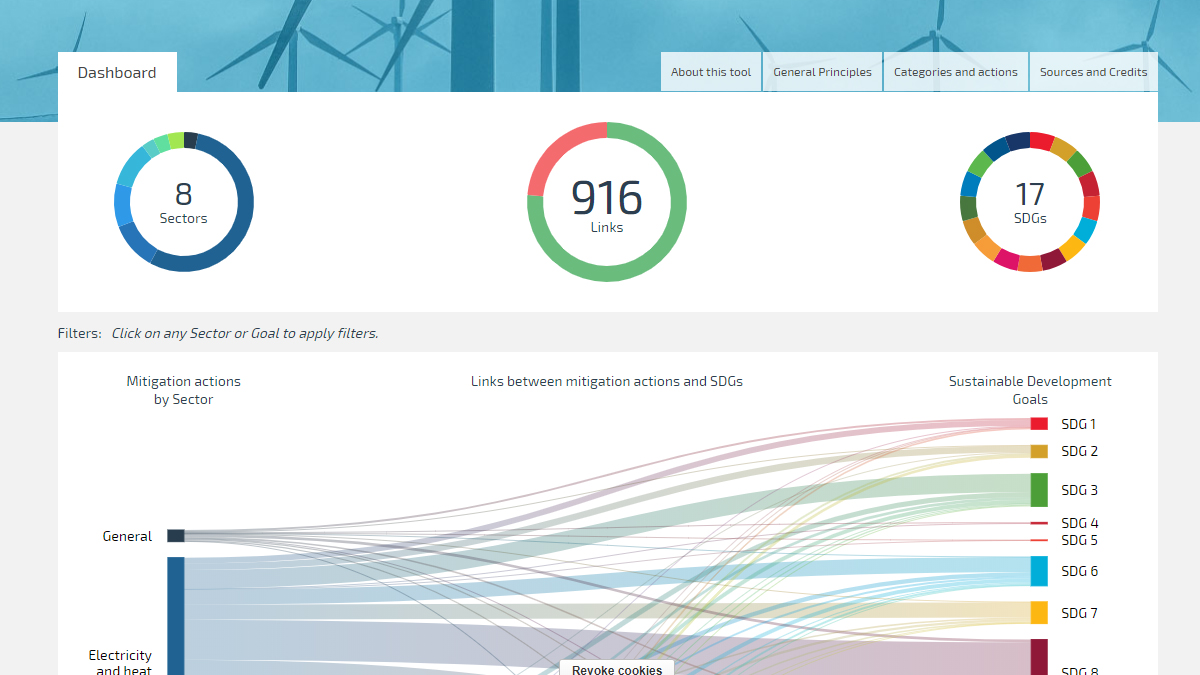 SCAN tool NewClimate Institute17 junho 2024
SCAN tool NewClimate Institute17 junho 2024 -
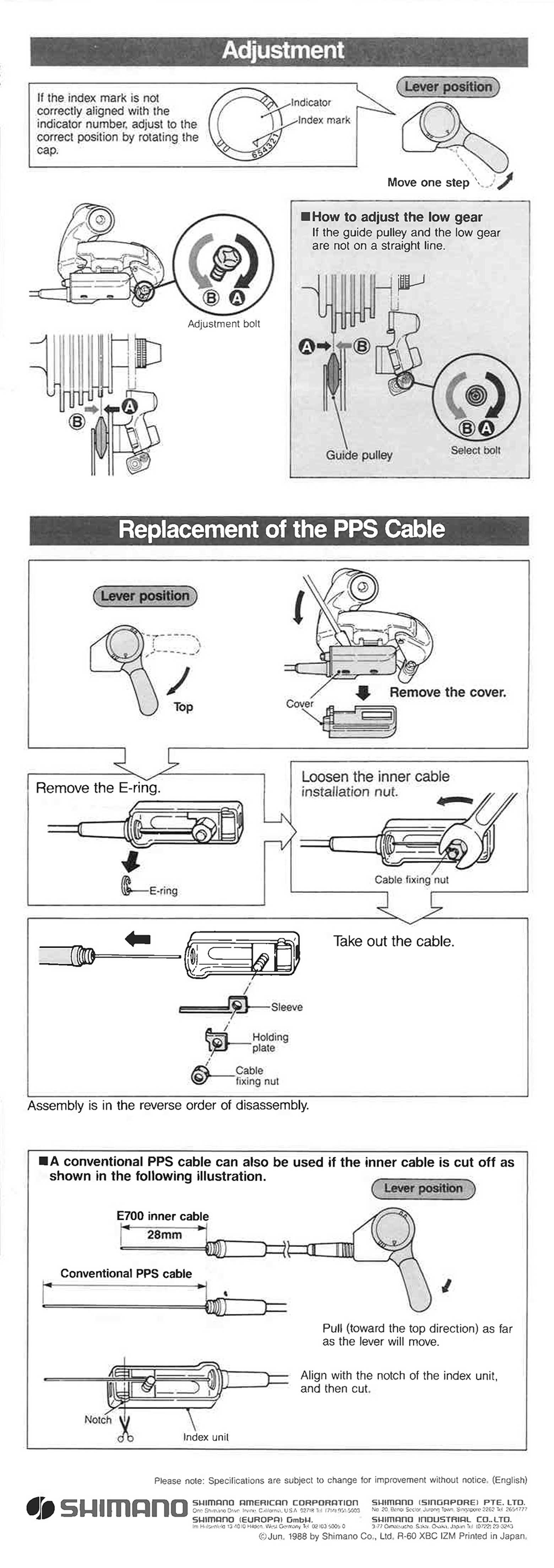 Shimano - Service Instructions Nexus RD-E700 Rear Derailleur scan 217 junho 2024
Shimano - Service Instructions Nexus RD-E700 Rear Derailleur scan 217 junho 2024 -
 Book Copy and Scan Systems - Nexus Imaging Solutions17 junho 2024
Book Copy and Scan Systems - Nexus Imaging Solutions17 junho 2024
você pode gostar
-
Russian Alphabet Lore Humanized Part 1217 junho 2024
-
 Himura Kenshin, Ultimate Pop Culture Wiki17 junho 2024
Himura Kenshin, Ultimate Pop Culture Wiki17 junho 2024 -
 Poppy Playtime Mommy Long Legs Plush Toy Poppy Playtime Huggy Wuggy Plush - Game - Aliexpress17 junho 2024
Poppy Playtime Mommy Long Legs Plush Toy Poppy Playtime Huggy Wuggy Plush - Game - Aliexpress17 junho 2024 -
 T-SHIRT ESTONADA Yu Yu Hakusho personagens R$58,43 em Samuel Bizin17 junho 2024
T-SHIRT ESTONADA Yu Yu Hakusho personagens R$58,43 em Samuel Bizin17 junho 2024 -
 The Maze Runner Review – Eggplante!17 junho 2024
The Maze Runner Review – Eggplante!17 junho 2024 -
 silly character maker|Picrew17 junho 2024
silly character maker|Picrew17 junho 2024 -
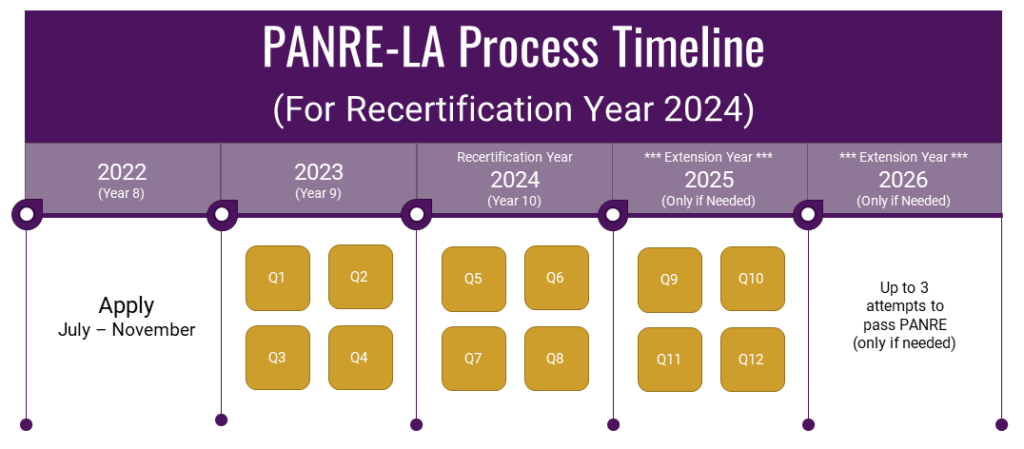 Maintain Certification - NCCPA17 junho 2024
Maintain Certification - NCCPA17 junho 2024 -
 Connie Talbot - Matters To Me - Out Today!!!17 junho 2024
Connie Talbot - Matters To Me - Out Today!!!17 junho 2024 -
Warriors: The New Prophecy : Free Download, Borrow, and Streaming17 junho 2024
-
 Sono Bisque Doll wa Koi o Suru Anime e Manga - Zona Crítica17 junho 2024
Sono Bisque Doll wa Koi o Suru Anime e Manga - Zona Crítica17 junho 2024

